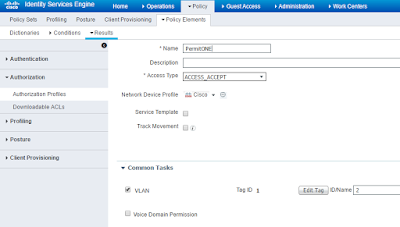
It is actually very simple.
1st:
You build out you ISE policies just as you would for Wired.1x or Wireless.1x and make sure to add the VLAN assignment to the authorization result that you match.
2nd:
On your WLC, make sure that your SSID has the box for Flexconnect local switching checked and AAA override checked on the advanced tab.
Make sure that you AP has VLAN support turned on and a local VLAN (Native) configured.
3rd:
Create a flexconnect group on your WLC from the wireless tab and add your APs to that group.
From the AAA VLAN-ACL mapping tab, create all of the VLANs that you will need to add users to from dynamic ISE assignments.
This will cause sub-interfaces to be auto-generated on all of your APs in that flexconnect group.
Finally:
Test a user/device that ISE will assign to one of the VLANs and verify that they are authenticated and placed into the desired VLAN. If everything connects you are good to go.
ISE
WLC
TIPS:
Make sure your VLANs are extended to the switch that the AP is connected to.
Make sure the WLC is running code level 7.4 or higher.